What is Tauri 2.0? Architecture and Core Features Explained
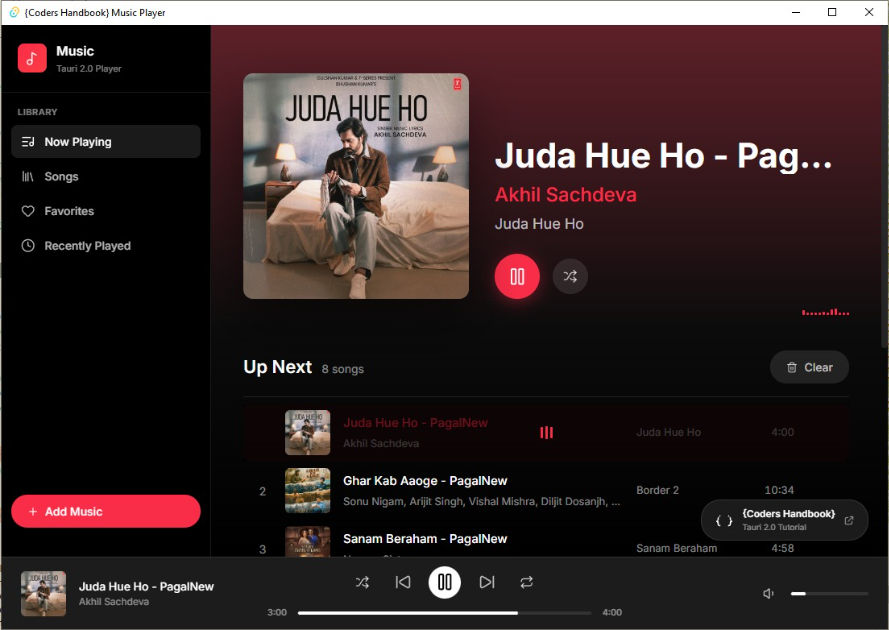
Tauri 2.0 is an innovative open-source framework that revolutionizes desktop application development by combining web frontend technologies (HTML, CSS, JavaScript, React, Vue, Svelte) with a secure Rust backend, leveraging the operating system's native WebView for rendering instead of bundling Chromium like Electron, resulting in dramatically smaller application bundles (3-5MB versus 150MB+), reduced memory consumption (50-100MB versus 200-500MB), faster startup times (under 1 second), enhanced security through sandboxing and Content Security Policy, and native performance through Rust's memory safety and zero-cost abstractions making it the ideal framework for building modern cross-platform desktop applications in 2026. This architectural approach represents a paradigm shift in desktop development, where developers can leverage familiar web technologies for UI development while utilizing Rust's powerful systems programming capabilities for backend operations, file system access, native API integration, and performance-critical tasks. Understanding Tauri's architecture is crucial for building efficient, secure, and maintainable desktop applications that deliver native-like experiences with web development velocity. This comprehensive guide explores Tauri 2.0's core architecture components, the WebView rendering system and its platform-specific implementations, the Rust backend and its role in application logic, Inter-Process Communication (IPC) mechanisms enabling frontend-backend interaction, the plugin system for extensibility, security model and sandboxing approach, and how all these components work together to create a cohesive desktop application framework. Whether you're migrating from Electron, exploring desktop development for the first time, or seeking to understand Tauri's technical foundations, this deep dive provides the architectural knowledge needed to build production-ready applications. Before proceeding, review the Tauri 2.0 beginner's guide for foundational concepts.
Tauri 2.0 Architecture Overview
Tauri 2.0 follows a multi-process architecture separating frontend presentation from backend logic through distinct processes that communicate via secure IPC channels. The architecture consists of the WebView Process (rendering UI using platform-native WebView), the Core Process (Rust backend handling system operations), the IPC Bridge (secure message passing between processes), and the Plugin System (modular extensions for additional functionality). This separation provides security benefits through process isolation, stability through independent process management, and performance through efficient resource allocation.
┌─────────────────────────────────────────────────────────────┐
│ TAURI APPLICATION │
├─────────────────────────────────────────────────────────────┤
│ │
│ ┌─────────────────────┐ ┌────────────────────┐ │
│ │ WebView Process │ │ Core Process │ │
│ │ (Frontend/UI) │◄───────►│ (Rust Backend) │ │
│ ├─────────────────────┤ IPC ├────────────────────┤ │
│ │ • HTML/CSS/JS │ │ • Commands │ │
│ │ • React/Vue/Svelte │ │ • State Management │ │
│ │ • Tauri APIs │ │ • File System │ │
│ │ • Event Listeners │ │ • Native APIs │ │
│ └─────────────────────┘ │ • Business Logic │ │
│ │ └────────────────────┘ │
│ │ │ │
│ ┌────────▼────────┐ ┌───────▼────────┐ │
│ │ Native WebView │ │ System APIs │ │
│ ├─────────────────┤ ├─────────────────┤ │
│ │ • WebKit (macOS)│ │ • File System │ │
│ │ • WebView2 (Win)│ │ • Networking │ │
│ │ • WebKitGTK (Lnx)│ │ • Clipboard │ │
│ └─────────────────┘ │ • Notifications │ │
│ └─────────────────┘ │
└─────────────────────────────────────────────────────────────┘WebView Layer - Platform Native Rendering
Tauri 2.0 utilizes the operating system's native WebView for rendering the user interface, eliminating the need to bundle Chromium and resulting in 97% smaller application bundles. On Windows, Tauri uses Microsoft Edge WebView2 (based on Chromium, pre-installed on Windows 10/11), on macOS it leverages WebKit (the same engine powering Safari, built into macOS), and on Linux it uses WebKitGTK (the GNOME web rendering engine). This approach means applications automatically benefit from OS-level updates and security patches, use consistent rendering with other system applications, consume significantly less disk space and memory, and start faster without initializing a bundled browser engine.
| Platform | WebView Engine | Pre-installed | Size Impact |
|---|---|---|---|
| Windows 10/11 | Edge WebView2 (Chromium) | Yes (built-in) | 0 MB (uses system) |
| macOS | WebKit (Safari engine) | Yes (built-in) | 0 MB (uses system) |
| Linux | WebKitGTK | Usually (apt/dnf) | 0 MB (system library) |
| Electron (comparison) | Bundled Chromium | No (bundled) | 100-150 MB per app |
Rust Core - Backend Logic and System Access
The Rust backend serves as the application's core, handling all system-level operations, business logic, file access, database interactions, and security-critical code with memory safety guarantees. Rust provides zero-cost abstractions meaning high-level code compiles to efficient machine code without runtime overhead, memory safety without garbage collection preventing common bugs like null pointer dereferences and buffer overflows, concurrency without data races through ownership and borrowing rules, and native performance comparable to C/C++. The Rust core manages command handlers that frontend can invoke, state management across application lifecycle, asynchronous operations using Tokio runtime, plugin system integration, and direct system API access. Learn more about creating Rust commands.
// Example Rust Core Structure
// src-tauri/src/main.rs
use tauri::State;
use std::sync::Mutex;
// Application state (shared across commands)
struct AppState {
counter: Mutex<i32>,
config: Mutex<AppConfig>,
}
struct AppConfig {
api_key: String,
theme: String,
}
// Command handler - callable from frontend
#[tauri::command]
fn process_data(data: String, state: State<AppState>) -> Result<String, String> {
// Perform CPU-intensive operations in Rust
let processed = data.to_uppercase();
// Update shared state
let mut counter = state.counter.lock().unwrap();
*counter += 1;
Ok(format!("Processed: {} (count: {})", processed, *counter))
}
// Async command for I/O operations
#[tauri::command]
async fn fetch_data(url: String) -> Result<String, String> {
// Async HTTP request using reqwest
let response = reqwest::get(&url)
.await
.map_err(|e| e.to_string())?
.text()
.await
.map_err(|e| e.to_string())?;
Ok(response)
}
// File system operation
#[tauri::command]
fn save_file(path: String, content: String) -> Result<(), String> {
std::fs::write(&path, content)
.map_err(|e| format!("Failed to save file: {}", e))
}
fn main() {
tauri::Builder::default()
.manage(AppState {
counter: Mutex::new(0),
config: Mutex::new(AppConfig {
api_key: String::new(),
theme: "dark".to_string(),
}),
})
.invoke_handler(tauri::generate_handler![
process_data,
fetch_data,
save_file
])
.run(tauri::generate_context!())
.expect("error while running tauri application");
}IPC Bridge - Frontend-Backend Communication
Inter-Process Communication (IPC) in Tauri 2.0 enables secure, type-safe communication between the WebView frontend and Rust backend through two primary mechanisms: Commands (request-response pattern where frontend invokes Rust functions) and Events (publish-subscribe pattern for asynchronous messaging). The IPC layer serializes data using JSON, validates permissions through allowlist configuration, enforces Content Security Policy restrictions, and provides TypeScript type definitions generated from Rust command signatures ensuring compile-time type safety. Unlike Electron's Node.js integration which exposes full system access to frontend code creating security vulnerabilities, Tauri's IPC requires explicit command registration making only authorized functions accessible. Learn more about IPC communication patterns.
// Frontend: Invoking Rust commands
import { invoke } from '@tauri-apps/api/tauri';
import { listen } from '@tauri-apps/api/event';
// Command invocation (request-response)
async function processUserData(data: string): Promise<string> {
try {
// Call Rust command 'process_data'
const result = await invoke<string>('process_data', { data });
return result;
} catch (error) {
console.error('Command failed:', error);
throw error;
}
}
// Event listening (publish-subscribe)
listen<ProgressUpdate>('download-progress', (event) => {
console.log('Download progress:', event.payload.percent);
updateProgressBar(event.payload.percent);
});
// Emit event from frontend to backend
import { emit } from '@tauri-apps/api/event';
await emit('user-action', { action: 'button-clicked', timestamp: Date.now() });
// Type-safe invocation with TypeScript
interface FileData {
path: string;
content: string;
}
interface SaveResult {
success: boolean;
message: string;
}
async function saveFile(fileData: FileData): Promise<SaveResult> {
return await invoke<SaveResult>('save_file', {
path: fileData.path,
content: fileData.content
});
}// Backend: Emitting events from Rust
use tauri::Manager;
#[derive(Clone, serde::Serialize)]
struct ProgressUpdate {
percent: f32,
message: String,
}
#[tauri::command]
async fn download_file(app: tauri::AppHandle, url: String) -> Result<(), String> {
// Simulate download with progress updates
for i in 0..=100 {
tokio::time::sleep(tokio::time::Duration::from_millis(50)).await;
// Emit event to frontend
app.emit_all("download-progress", ProgressUpdate {
percent: i as f32,
message: format!("Downloading... {}%", i),
}).map_err(|e| e.to_string())?;
}
Ok(())
}
// Listen to frontend events in Rust
fn setup_event_listeners(app: &mut tauri::App) -> Result<(), Box<dyn std::error::Error>> {
let app_handle = app.handle();
app.listen_global("user-action", move |event| {
if let Some(payload) = event.payload() {
println!("Received user action: {}", payload);
// Process event...
}
});
Ok(())
}Plugin System - Modular Extensions
Tauri 2.0's plugin system enables modular functionality through official and community-developed plugins that extend core capabilities without modifying the framework itself. Official plugins include tauri-plugin-store (persistent key-value storage), tauri-plugin-sql (SQLite database integration), tauri-plugin-http (HTTP client), tauri-plugin-fs (enhanced file system access), and tauri-plugin-notification (desktop notifications). Plugins follow a consistent API pattern providing Rust backend functionality, JavaScript/TypeScript bindings for frontend access, automatic permission management, and cross-platform compatibility. Developers can create custom plugins to encapsulate reusable functionality across projects or share with the community.
// Using official plugins
// Cargo.toml
[dependencies]
tauri-plugin-store = "2.0"
tauri-plugin-sql = { version = "2.0", features = ["sqlite"] }
tauri-plugin-notification = "2.0"
// src-tauri/src/main.rs
use tauri_plugin_store::StoreBuilder;
use tauri_plugin_sql::{SqlitePool, Migration};
fn main() {
tauri::Builder::default()
// Register store plugin
.plugin(tauri_plugin_store::Builder::default().build())
// Register SQL plugin with migrations
.plugin(tauri_plugin_sql::Builder::default()
.add_migrations(
"sqlite:app.db",
vec![
Migration {
version: 1,
description: "create users table",
sql: "CREATE TABLE users (id INTEGER PRIMARY KEY, name TEXT)",
kind: tauri_plugin_sql::MigrationKind::Up,
}
],
)
.build())
// Register notification plugin
.plugin(tauri_plugin_notification::init())
.run(tauri::generate_context!())
.expect("error while running tauri application");
}// Frontend: Using plugins
import { Store } from '@tauri-apps/plugin-store';
import Database from '@tauri-apps/plugin-sql';
import { sendNotification } from '@tauri-apps/plugin-notification';
// Persistent store
const store = new Store('settings.json');
await store.set('theme', 'dark');
const theme = await store.get<string>('theme');
// SQLite database
const db = await Database.load('sqlite:app.db');
await db.execute('INSERT INTO users (name) VALUES (?)', ['John Doe']);
const users = await db.select<Array<{id: number, name: string}>>(
'SELECT * FROM users'
);
// Desktop notification
await sendNotification({
title: 'Task Complete',
body: 'Your file has been processed successfully',
icon: 'success'
});Security Model and Sandboxing
Tauri 2.0 implements multiple security layers to protect against common desktop application vulnerabilities. The Content Security Policy (CSP) prevents XSS attacks by restricting script sources, the Allowlist System explicitly defines which APIs frontend can access, Process Isolation separates WebView from Core preventing direct system access, IPC Validation ensures only registered commands are executable, and No Node.js Integration eliminates entire classes of vulnerabilities present in Electron. By default, Tauri applications run with minimal permissions requiring developers to explicitly enable features like file system access, networking, or shell execution creating a secure-by-default environment. Learn more about Tauri security implementation.
| Security Feature | Tauri 2.0 | Electron |
|---|---|---|
| Process Isolation | ✅ Frontend & Backend separated | ⚠️ Node.js in renderer possible |
| Content Security Policy | ✅ Enforced by default | ⚠️ Optional, often disabled |
| API Access | ✅ Explicit allowlist required | ❌ Full Node.js access possible |
| Command Registration | ✅ Only registered commands accessible | ❌ Any Node.js code executable |
| Dependency Vulnerabilities | ✅ Rust's cargo ecosystem | ⚠️ npm/Node.js vulnerabilities |
| Remote Code Execution | ✅ Prevented by sandboxing | ⚠️ Possible with Node.js access |
Application Lifecycle
Understanding the Tauri application lifecycle is essential for proper initialization, state management, and cleanup. The lifecycle begins with Initialization (Rust runtime starts, plugins load, state initializes), proceeds to Setup (custom setup functions execute, event listeners register, database connections establish), continues with Window Creation (WebView initializes, frontend loads, IPC bridge activates), operates during Runtime (commands process, events flow, state updates), and concludes with Shutdown (cleanup handlers execute, resources release, graceful exit). Developers can hook into lifecycle events to perform initialization tasks, cleanup operations, and state persistence.
// Application lifecycle management
use tauri::Manager;
fn main() {
tauri::Builder::default()
// Setup hook - runs before window creation
.setup(|app| {
println!("Application starting...");
// Initialize database
init_database()?;
// Load configuration
let config = load_config()?;
app.manage(config);
// Register global event listeners
let app_handle = app.handle();
app.listen_global("app-ready", move |_event| {
println!("Frontend is ready!");
});
Ok(())
})
// Window creation hook
.on_window_event(|event| match event.event() {
tauri::WindowEvent::CloseRequested { api, .. } => {
println!("Window closing...");
// Perform cleanup
save_state();
// Allow window to close
}
tauri::WindowEvent::Focused(focused) => {
if *focused {
println!("Window gained focus");
} else {
println!("Window lost focus");
}
}
_ => {}
})
// Application shutdown hook
.on_page_load(|window, _payload| {
println!("Page loaded in window: {}", window.label());
})
.run(tauri::generate_context!())
.expect("error while running tauri application");
}
fn init_database() -> Result<(), Box<dyn std::error::Error>> {
println!("Initializing database...");
// Database setup code
Ok(())
}
fn load_config() -> Result<AppConfig, Box<dyn std::error::Error>> {
println!("Loading configuration...");
// Configuration loading
Ok(AppConfig::default())
}
fn save_state() {
println!("Saving application state...");
// State persistence
}Core Features and Capabilities
- Native WebView Integration: Platform-specific rendering engine (Edge WebView2, WebKit, WebKitGTK) with zero bundle size impact
- Rust Backend: Memory-safe systems programming language for performance-critical operations and system access
- Type-Safe IPC: Automatic TypeScript type generation from Rust commands ensuring compile-time safety
- Multi-Window Support: Create multiple windows, manage window state, communicate between windows
- File System Access: Read/write files, directory operations, file dialogs with security validation
- System Integration: System tray, notifications, global shortcuts, clipboard access
- Auto-Update System: Built-in updater supporting GitHub releases, custom update servers
- Plugin Ecosystem: Official and community plugins extending functionality modularly
- Cross-Platform Build: Single codebase compiles to Windows, macOS, Linux, iOS, Android
- Development Tools: Hot reload, DevTools integration, CLI tooling, comprehensive debugging
Architecture Comparison with Alternatives
| Aspect | Tauri 2.0 | Electron | Native (Qt/GTK) |
|---|---|---|---|
| Rendering | OS WebView | Bundled Chromium | Native widgets |
| Backend Language | Rust | Node.js/JavaScript | C++/Python/Go |
| Frontend | Web technologies | Web technologies | Platform-specific |
| Bundle Size | 3-5 MB | 150-200 MB | 10-50 MB |
| Memory Usage | 50-100 MB | 200-500 MB | 30-100 MB |
| Startup Time | < 1 second | 2-5 seconds | < 1 second |
| Security Model | Sandboxed + CSP | Optional isolation | Platform-dependent |
| Development Speed | Fast (web tech) | Fast (web tech) | Moderate (native APIs) |
| Cross-Platform | Desktop + Mobile | Desktop only | Requires separate builds |
Next Steps
- Compare with Electron: Detailed framework comparison at Tauri vs Electron
- Install Tauri: Set up development environment with installation guide
- Build First App: Hands-on tutorial at creating your first Tauri app
- Understand Project Structure: Learn file organization at project structure guide
- Master IPC: Deep dive into communication at IPC patterns
Conclusion
Tauri 2.0's architecture represents a modern approach to desktop application development, combining the flexibility of web technologies with the performance and security of Rust and native operating system components. By understanding the WebView rendering layer, Rust backend capabilities, IPC communication mechanisms, plugin system extensibility, security model implementation, and application lifecycle management, developers can build efficient, secure, and maintainable desktop applications that deliver exceptional user experiences with minimal resource consumption. The architectural decisions in Tauri 2.0—using native WebViews instead of bundling browsers, employing Rust for backend operations, implementing secure process isolation, and providing modular plugin extensibility—result in applications that are lighter, faster, more secure, and more resource-efficient than traditional Electron applications while maintaining the development velocity advantages of web technologies. As desktop application requirements evolve toward smaller bundles, enhanced security, and cross-platform compatibility including mobile devices, Tauri's architecture positions it as the framework of choice for modern application development.
$ share --platform
$ cat /comments/ (0)
$ cat /comments/
// No comments found. Be the first!